Security Overrides
The security override feature in EPASS allows authorized users to bypass system restrictions, such as selling a product below the minimum sell price, scheduling a COD invoice that has a balance owing, or deleting invoices. You can employ a single password override policy or a user-based override policy. User-based is more secure and is logged for accountability, whereas a single password policy is much less strict.
Setting Up Security Overrides
Security overrides are set up in Invoicing Variables.
-
Go to Tools > System Maintenance, and then click the Variables tab.
-
Click Invoicing, and then click Open.
-
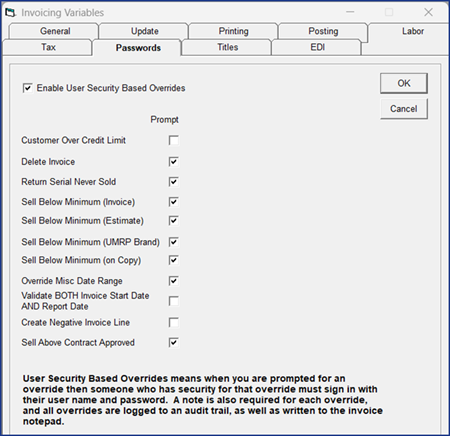
Click the Passwords tab.
User-Based Overrides
Setting up a user-based override policy requires you to select which system actions require an override prompt, and then assigning override security to each authorized user or group.
Select Override Prompts
-
Select Enable User Security Based Overrides.
-
Select each action that requires an override prompt.
-
Click OK to close Invoicing Variables.
Assign Override Security Options
-
Go to Tools > System Maintenance, and then click the Tables tab.
-
Click User Security, and then click Open.
-
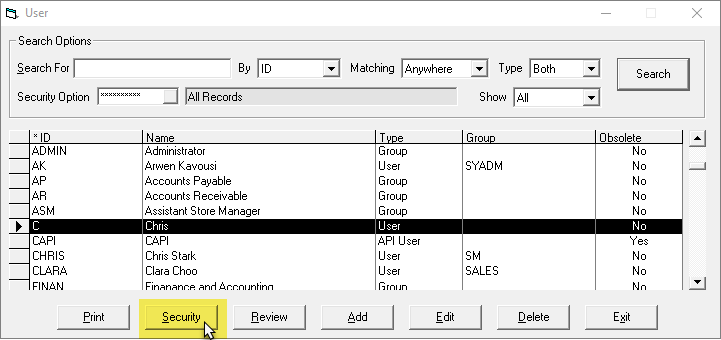
Select a User or Group, and then click Security.
-
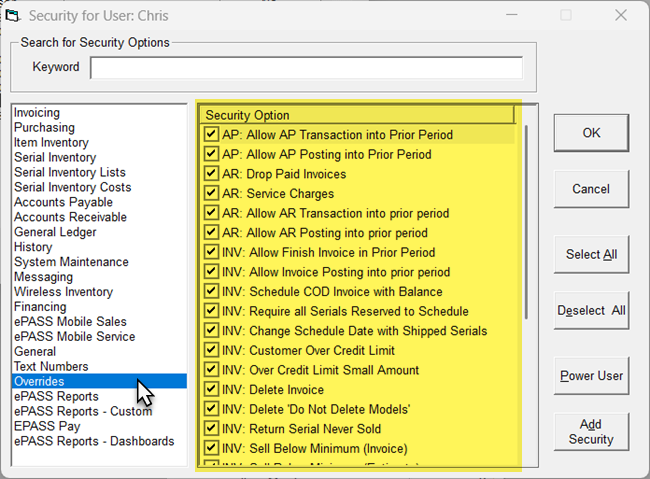
Select the Overrides section. In the overrides section of user security, you establish which overrides each user has security for. If you have override security in an area, EPASS still prompts you for an override, but you don't have to type in your user ID and password.
-
When finished, click OK.
-
Repeat steps 3–5 for additional users or groups.
Single Password Overrides
A single password override policy is faster and easier to setup and use, at the cost of being less secure and accountable than a user-based policy. There is no user logging, which means you won't know who authorized the override, and a single password can be easily shared among users.
Steps
-
Clear Enable User Security Based Overrides.
-
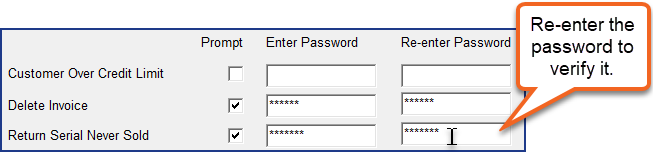
Select each action that requires an override prompt and enter a unique password. The user will need to enter this password when prompted to override the action in EPASS.
-
Click OK to close Invoicing Variables.
Override Examples
Invoicing
Most of the override securities are focused around the invoicing system. In this example, the user is attempting to schedule a COD invoice with a balance owing.
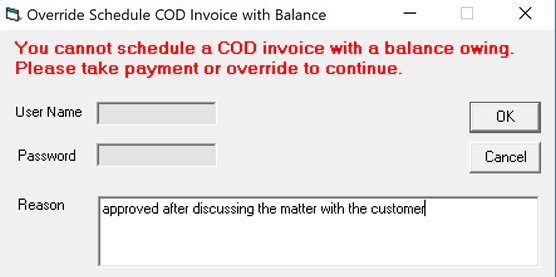
The user name and password are greyed out, which indicates that the user signed into EPASS has security to override this action, so all EPASS requires is a reason for the override.
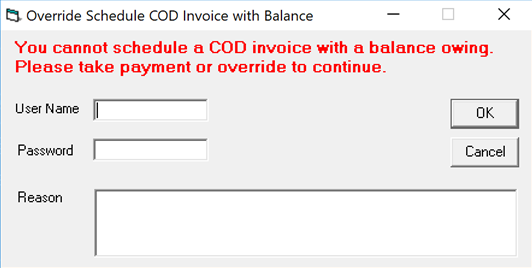
In the next example, the user logged into EPASS does not have override security to schedule a COD invoice with a balance owing and must get a manager or supervisor with override security to enter their user ID, password, and an override reason.
Override Logging (Invoicing)
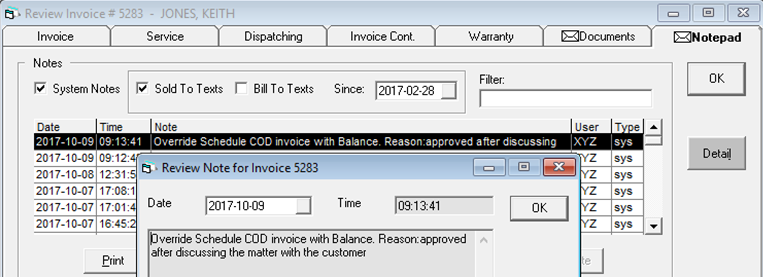
When an invoicing action is overridden, EPASS generates a system note with the date, time, user details, and the reason in the invoice Notepad. The user ID in the system note is the person who authorized the override.
See Also
November 26, 2025